Renegotiation, Downgrade and Cross Protocol Attacks Against SSL/TLS
In previous Article we have discussed about “What is SSL Certificate and How it Works ?” and there are various possible attacks made in the previous SSL Versions as Renegotiation Attack, Downgrade Attack and Cross Protocol Attacks as explained below.
Renegotiation Attack
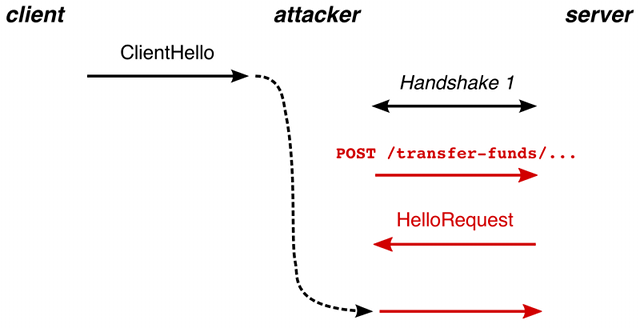
The Renegotiation Attack is the Plain Text Injection Attack procedure against SSL 3.0 and all versions of the TLS which is discovered in August 2009. Through this attack, the attacker will splice their own request into beginning of the request made by the client through web browser with the server. The Attacker can’t decry-pt the messages send by the client person, so it won’t come under the Man in the Middle Attack. To fix this and to avoid these attacks, the renegotiation were stopped from the web server so that there will not be any changes in the communication unless the client certificate is used.
FREAK attack and Logjam attack (Downgrade attacks)
The protocol downgrade attacks is also called as version rollback attacks. Due to this attack, the web browser will negotiate to get connected with previous versions of TLS Protocols which is insecure.
Encryption downgrade attacks will force the clients (Web browser) and the web server to communicate with the cryptographically weak keys. Freak – Man in the Middle Attack on OpenSSL Stack was discovered on the year 2014. This attack is made by negotiating the servers to use cryptographically weak encryption keys (512 bit).
Logjam Attack was discovered in the May 2015 which is the security exploits, that is done through the option of using legacy “export-grade”. It downgrades the susceptible servers to cryptographically weak 512-bit Diffie–Hellman groups.

DROWN (Cross-protocol attacks)
This Attack is made in the servers that supports contemporary SSL/TLS protocol suites by exploiting the unused ports or connections. The full details of DROWN Attacks was announced by March 2016 and it is made by exploiting the vulnerability in the Protocols and server configuration. All types of servers that offer services encrypted with the TLS which supports the SSLv2, that shares the same public key credentials between the two protocols. During the detailed release about the DROWN Attack, they also released the Patch with which alone we can’t stop the DROWN Attack and it can be avoided by disabling the SSLv2.